(Editor’s Note: This article represents part five of an ongoing series. Part one, appeared on August 18, entitled “The Unavoidable ‘SCREAM’: Why Enterprise Architecture Must Transform for the Organization of Tomorrow“, introduced the conceptual overview. Part two, “The Anatomy of SCREAM: A Perfect Storm in EA Cupboard” detailed the current state of chaotic SCREAM. Part three, “The Co-Architect EA: Enterprise AARAM Through AI” detailed the aspirational future state of blissful AARAM. Part four “TRIAL: Charting the Path from SCREAM to AARAM – A Simplified Guide for Effective Enterprise Architecture” that highlighted the three prong approach/bridge to AARAM. This installment introduces BITS & BYTES— the first lens to simplify the Enterprise )
The complexity of modern technology landscapes demands a simpler, more powerful foundational language for Enterprise Architecture (EA). Here is the first core of TRIAL: BITS & BYTES—the essential lens to simplify foundational constructs and effectively leverage existing architectural practices. This paradigm serves as a strategic guardrail for managing architectural change at its most granular level.
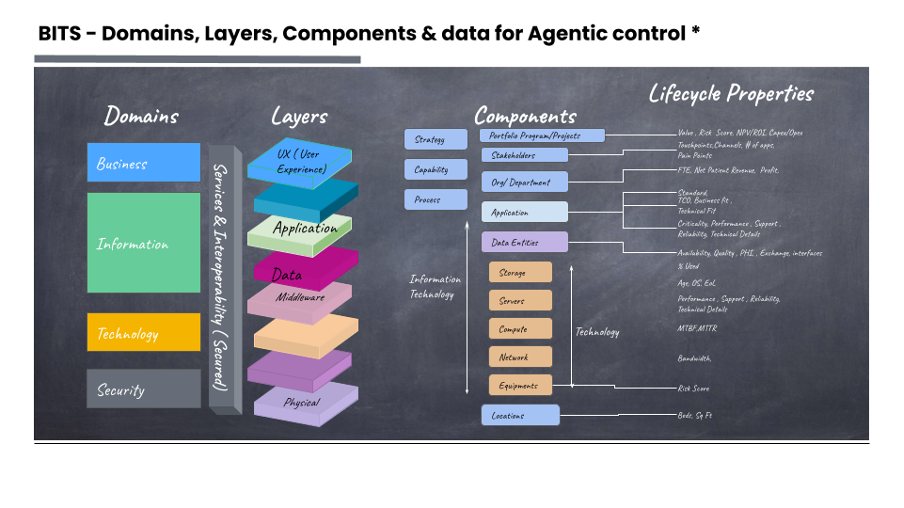
The Architecture Domains
These four high-level domains act as the atomic unit of enterprise architecture, providing the four indispensable coordinates for any  architectural component. This is a deliberate choice, diverging from descriptive models like BDAT (Business, Data, Application, Technology) found in other frameworks.
architectural component. This is a deliberate choice, diverging from descriptive models like BDAT (Business, Data, Application, Technology) found in other frameworks.
Why BITS, Not BDAT as Architecture Domains?
In the evolving realm of enterprise architecture, the BITS model emerges as an improved domain representation over traditional BDAT, particularly amid emerging technologies like quantum computing, which demand integrated security from the outset to avoid fragmented vulnerabilities and ensure resilient, forward-compatible structures.
This approach explicitly embeds security as a foundational domain through Enterprise Information Security Architecture (EISA), aligning with broader frameworks such as TOGAF, Zachman, ArchiMate, and FEAF. EISA formalizes BITS for proactive threat management in dynamic landscapes, contrasting BDAT’s silos that require constant reconfiguration.
The distinction establishes foundational balance and clarity:
- Holistic Consolidation of IT: BITS consolidates granular technical areas (Data, Application, Infrastructure) into two high-level pillars—Information (data management, knowledge assets, flow) and Technology (platforms, infrastructure, tech stack). This ensures the fundamental concern of data and its enabling technology is always addressed, allowing flexible decomposition without losing strategic focus.
- Explicit Security Pillar: The accelerating complexity of security—driven by cloud adoption, hybrid work, and quantum computing threats—dictates that Security must be an explicit, independent domain. BITS elevates security to an atomic pillar, ensuring it is a foundational consideration in every planning phase, not merely a compliance afterthought.
- The Foundational Gauge: The four BITS pillars are always present and necessary to gauge effective architectural maturity. The ultimate purpose of EA is defined at this atomic level: managing every “bit” securely across the “bytes” processing. This simple yet powerful language ensures complex concepts remain manageable for all stakeholders.
BITS serves as high-level strategic governance—ensuring balanced maturity assessments across business alignment, information-centric decision-making, technology enablement, and security resilience—while leveraging BDAT’s detailed sub-domains (layers and components) for tactical implementation and operational oversight. This allows organizations to maintain BDAT’s precision in decomposing complex IT landscapes (e.g., mapping specific data architectures or application portfolios) within BITS’s overarching pillars, fostering adaptive governance that scales from atomic “bits” of change to enterprise-wide transformations
BYTES: The Guiding Force and Lifecycle Derivative

If BITS defines what must be managed, BYTES (Balanced Yearly Transformation to Enhance Services) define how change must be processed. BYTES is more than a set of principles; it is a derivative of the core architectural lifecycle: Plan (Balanced Yearly), Design& Build (Transformation Enhancing) , and Run (Services). Each component of BYTES directly maps to the mandatory stages of a continuous transformation framework, enabling architects to manage change at its source.
This guiding force acknowledges that transformation is not a singular event but a continuous process that can be further decomposed into multiple stages (e.g., portfolio planning, capability modelling, solution architecture, software engineering, and continuous deployment). BYTES serves as the overarching guardrails that facilitate systematic, controlled, and business-aligned change across the entire organization.
The BYTES Guardrails: Governance in Practice across Lifecycle
Each letter of BYTES is a critical guardrail, ensuring that transformation remains strategically aligned and risk-aware:
- B – Balanced (The Governance Guardrail): Ensures every initiative is assessed against all four BITS This prevents architectural drift where projects optimize for one domain at the expense of others, mandating holistic trade-off discussions at the planning stage.
- Y – Yearly (The Strategic Alignment Guardrail): Elevates transformation from ad-hoc projects to an aligned operational strategy. This transforms static strategic plans into active, living roadmaps, forcing clarity on the Information required to reach the next level of transformation and revealing its digital footprint across your application landscape.
- T – Transformation (The Change Management Guardrail): Focuses on rigorous lifecycle change management discipline. This ensures changes—whether incremental or disruptive—are executed strategically with clear measurement criteria and minimal disruption, ensuring design decisions map back to Business domain strategic intent.
- E – Enhancing (The Value Guardrail): Ensures every change drives measurable improvement through operational efficiency, new revenue streams, or improved resilience. It compels architects to continuously seek better ways of delivering value throughout the Run
- S – Services (The Delivery Guardrail): Ensures the ultimate goal of any architectural change is to enhance services provided to customers or internal users. This forces an external, customer-centric view onto internal technical workings, completing the feedback loop of the Run
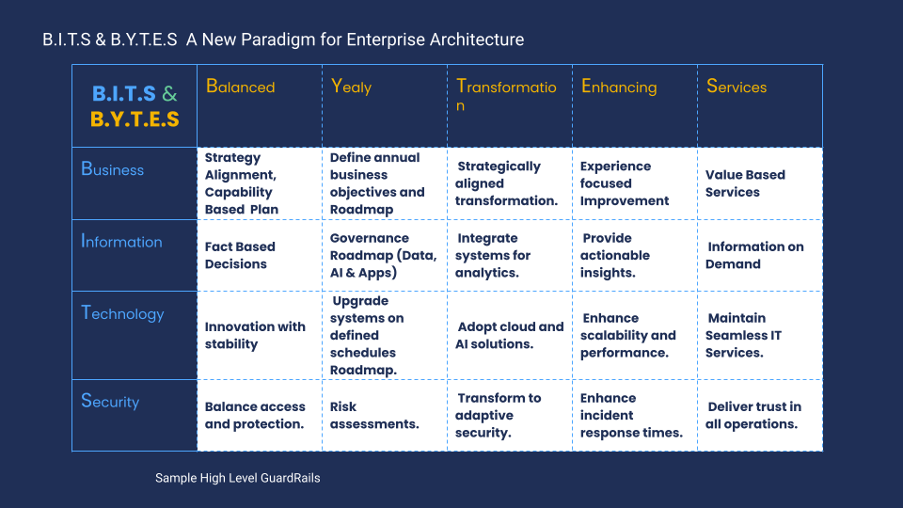
This initial BITS & BYTES matrix provides the principle-level view—the 4×5 table of governance guardrails. This view is necessary for communication and strategic alignment.
The BITS & BYTES Matrix: A Meta-Gateway for Existing Models
The BITS & BYTES framework is not intended to replace existing architecture frameworks (e.g., TOGAF, Zachman, DAMA, IT4IT, SAFe). Instead, it acts as a meta-framework—a simplified, high-level matrix that accommodates and contextualizes the applicability of all existing models.
This approach responds to a persistent call echoed throughout our professional community: the need for an all-encompassing EA body of knowledge that unifies disparate frameworks under a common, coherent language.
This matrix allows an enterprise to objectively assess where each existing framework excels:
- Applicability Mapping: A governance team can map TOGAF’s ADM primarily against the Business and Technology BITS domains within the Plan and Design BYTES lifecycle stages. Simultaneously, DAMA’s DMBoK would map heavily against the Information domain, predominantly across the Yearly and Enhancing BYTES principles.
- Gap Identification: This matrix easily highlights gaps. If an organization finds no existing framework maps strongly to the Security domain across the Transformation lifecycle, that represents a clear, actionable governance gap. Some frameworks might be excellent at multiple intersections, while others might not be applicable at all, which is a key insight for EA leadership.
Exploding to the Component Level: The Future of Implementation
The true power of this framework will be realized by “exploding” the matrix to the detailed component level.
In our next instalment, we will detail how to use the BITS & BYTES framework to:
- Decompose each BITS domain into its constituent architectural components (e.g., Information to Data Entities, Technology to Platform Services).
- Map the lifecycle stages of BYTES (Plan, Design, Run) to practical implementation activities—from portfolio management and solution architecture to Software Engineering and continuous Management.
- Show how this granular mapping allows architects to collect, store, and leverage detailed lifecycle change information for every single component, transforming the abstract concept of an “atomic unit” into a tangible, measurable practice.
Call to Action: Join the Improvement Effort
This BITS & BYTES framework is a critical step in providing a unified language for our profession. We believe this simple, four-pillared domain model, guided by the five principles of the BYTES lifecycle, is the necessary first bridge to simplify and align complex transformation efforts.
Let’s collaborate to finalize this foundational language and create a durable, peer-validated standard that elevates the impact of Enterprise Architecture across the globe. Please reach out to share your findings to form a working group.
By establishing BITS as the foundational atomic language and BYTES as the guiding lifecycle force, we equip the enterprise with the necessary tools to navigate the complexity of modern architecture and achieve true, continuous transformation.
Appendix: References
- Wikipedia. “Shor’s Algorithm.” Overview of Shor’s algorithm, its quantum computing significance, and technical explanation.
- QUBIP. “The Role of Quantum Computers in Shor’s Algorithm.” Details on period finding and cryptographic impact in quantum computing.
- Classiq. “Shor’s Algorithm Explained.” Explanation of quantum cryptography and Shor’s algorithm’s quantum advantage over classical algorithms.
- Graves, Tom. “On BA and EA.” Tetradian, July 3, 2017. Discussion on business and enterprise architecture alignment.
- Graves, Tom. “Enterprise-Architects—Dump the BDAT-Stack!” LinkedIn. Critique of BDAT’s IT-centric limitations in enterprise architecture.
- Entasis Partners. “Comprehensive Analysis of TOGAF’s BDAT Model.” Analysis of the BDAT model within the TOGAF framework and its structured approach to aligning IT and business.
- SABSA Foundation. “SABSA White Paper: Enterprise Security Architecture.” Overview of SABSA’s security architecture framework, aligning security with business domains.
- IBM Institute for Business Value. “The Quantum Decade: A Playbook for Achieving Quantum Advantage.” Insights on quantum computing’s enterprise applications beyond cryptography.
- The Open Group. “TOGAF Standard, 10th Edition – Architecture Development Method (ADM).” Details on TOGAF’s lifecycle methodology, supporting BYTES’s governance structure.