
Dr. Magesh Kasthuri, Chief Architect & Distinguished Member of Technical Staff, Wipro Limited
Any cloud architecture requires five pillars of well-architected design to be satisfied to make it robust and fool proof. The five pillars include Performance efficiency, Security and compliance, Cost Optimization, Availability and Operational Efficiency. Developing cloud solutions for the U.S. Government requires strict adherence to the compliance of Federal Risk and Authorization Management Program (FedRAMP), a government-wide program that standardizes security assessment, authorization, and continuous monitoring for cloud products and services. This article outlines a comprehensive, Azure-specific strategy for building FedRAMP-compliant cloud applications.
Understanding the Compliance Landscape
FedRAMP compliance is categorized into three impact levels—Low, Moderate, and High—based on the sensitivity of the data handled. For example, if you consider Microsoft Azure cloud platform, Azure Government and Azure Government Secret offer services that are FedRAMP High and DoD IL5/6 certified, making them ideal for federal workloads.
Step 1: Assessing Cloud Readiness
Before initiating migration or development, conduct a thorough application assessment:
- Cloud Suitability Analysis: Evaluate the application’s architecture, dependencies, and data sensitivity.
- FedRAMP Whitelisting: Identify Azure services that are FedRAMP-authorized (e.g., Azure SQL Database, Azure Kubernetes Service, Azure API Management).
- Application Profiling: Use tools like Azure Migrate and Azure Advisor to assess infrastructure, licensing, and performance baselines.
Step 2: Designing a FedRAMP-Compliant Architecture
Key Architectural Principles
- Zero Trust Security: Implement identity-based access controls using Azure Active Directory (AAD) with Conditional Access and Multi-Factor Authentication (MFA).
- Hybrid Connectivity: Use Azure ExpressRoute for secure, private connections to on-premises systems.
- Data Protection: Ensure encryption at rest using Azure Storage Service Encryption and in transit using TLS 1.2+.
- High Availability: Deploy across Azure regions (e.g., East US and West US) with Azure Traffic Manager and Availability Zones.
Example Architecture Components
| Layer | Azure Services |
| UI/UX | Azure App Service, Angular/React frontend |
| API Layer | Azure API Management, Azure Functions |
| Business Logic | Azure Kubernetes Service (AKS) or Azure App Service |
| Data Layer | Azure SQL Database with Always Encrypted, Azure Blob Storage |
| Security | Azure Firewall, Azure DDoS Protection, Microsoft Defender for Cloud |
| Monitoring | Azure Monitor, Log Analytics, Application Insights |
Reference architecture for FedRAMP certified Azure solution
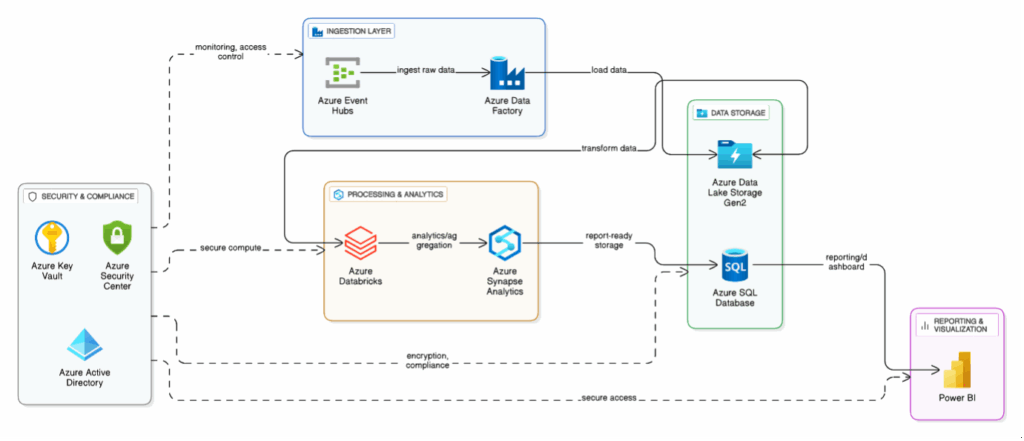 Figure: Azure Reference Architecture on Reconciliation and Reporting solution
Figure: Azure Reference Architecture on Reconciliation and Reporting solution
Step 3: Implementing DevSecOps
A secure CI/CD pipeline is essential for maintaining compliance and agility:
- Source Control: Azure Repos or GitHub Enterprise
- Build & Release: Azure Pipelines with integrated security scans (e.g., SonarCloud, WhiteSource)
- Infrastructure as Code: Use Bicep or Terraform for consistent, auditable deployments
- Security Gates: Integrate Microsoft Defender for DevOps to enforce security policies during builds
Step 4: Data Migration and Integration
For legacy systems and on-prem databases:
- Schema Conversion: Use Azure Database Migration Service (DMS) to convert and migrate schemas.
- Data Transfer: Securely transfer data using Azure Data Factory with private endpoints.
- API Integration: Connect to on-prem APIs via Azure API Management and ExpressRoute.
Step 5: Security and Compliance Framework
Identity and Access Management
- Use Azure AD for centralized identity management.
- Implement Role-Based Access Control (RBAC) and Privileged Identity Management (PIM).
Network Security
- Isolate workloads using Azure Virtual Network (VNet) and Network Security Groups (NSGs).
- Use Azure Private Link to access PaaS services securely.
Data Security
- Enable Transparent Data Encryption (TDE) and Always Encrypted for databases.
- Use Azure Key Vault for key management and secrets storage.
Threat Protection
- Enable Microsoft Defender for Cloud for threat detection and compliance posture management.
- Conduct regular penetration testing in accordance with FedRAMP guidelines.
Step 6: Testing and Validation
- Functional Testing: Validate application functionality across environments (Dev, QA, UAT, Prod).
- Security Testing: Perform vulnerability scans, static code analysis, and penetration testing.
- Performance Testing: Use Azure Load Testing to simulate user traffic and validate SLAs.
Step 7: Monitoring and Reporting
- Monitoring: Use Azure Monitor and Application Insights for real-time observability.
- Auditing: Enable Azure Activity Logs and Diagnostic Settings for compliance tracking.
- Reporting: Generate dashboards for usage, cost, and security metrics using Power BI or Azure Workbooks.
Step 8: Training and Handover
- Conduct workshops and training sessions for IT and business stakeholders.
- Provide documentation including runbooks, architecture diagrams, and compliance checklists.
Step 9: Governance and Continuous Compliance
- Establish a governance model with regular reviews and audits.
- Use Azure Policy to enforce compliance rules and automate remediation.
- Continuously monitor FedRAMP updates and align with evolving standards.
Conclusion
Developing FedRAMP-compliant cloud solutions on Azure requires a holistic approach that spans architecture, security, DevSecOps, and governance. This requires architecture that aligns with Azure’s native capabilities, organizations can confidently deliver secure, scalable, and compliant solutions for the U.S. Government.
