By Andy Ruth, of Sustainable Evolution
Change management isn’t any different for Zero Trust than it is for any other big initiative. But most of us aren’t very good at change management. And security and cybersecurity are not sexy. And most people want their security to be minimally invasive and as unnoticeable as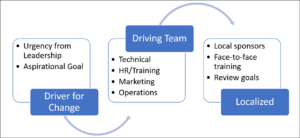 possible. And most leaders get no top-line/bottom-line joy from spending money on Zero Trust initiatives. And Zero Trust doesn’t drop new features and functionality for a product at the end of a sprint.
possible. And most leaders get no top-line/bottom-line joy from spending money on Zero Trust initiatives. And Zero Trust doesn’t drop new features and functionality for a product at the end of a sprint.
But you still need change management so that you can gain endorsement from leadership, drive urgency or aspiration in stakeholders and users, and drive long-term cultural change. Three key areas you can focus on as you get started:
- Get leadership engaged – If the culture of your organization is driven by urgency, craft a message and plan that leverages urgency. If the culture is driven through aspiration, use aspirational vision and goals. Either way, get leadership on board to deliver the message.
- Create a communications strategy – The strategy must include the rhythm and mode of communications, as well as the context and content of the communications for leadership and sponsors, leads and key centralized players, local mavens, and users. Persuasive communication is what the marketing team does well. Get them involved.
- Training, support, and rewards – The training does not need to be slick and pretty, but it does need to be informative and available. Online, through lunch-and-learns, recorded videos. Support must be available when someone gets stuff, and a recognition or reward system will help drive participation as a carrot, the annual review process as the stick.
There is a change management standard created to meet ISO specifications for standards creation, and several change management processes you can use to drive change. The rest of this article provides a brief description and example of usage for several, along with links you can use to investigate further.
ACMP
The Association of Change Management Professionals (ACMP) maintains a standard for change management that describes in about 70 pages how to create and drive a change management plan. Their standard shows a step for closing the change management process.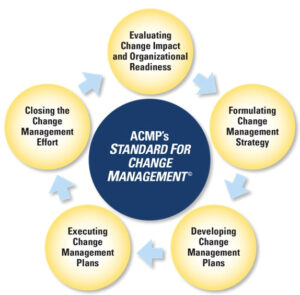 However, we feel that Zero Trust and cybersecurity are ongoing efforts that will always require change management so closing the effort might never occur. They also offer a certification, so if you are looking for a change management resource this is a good way to narrow down your search.
However, we feel that Zero Trust and cybersecurity are ongoing efforts that will always require change management so closing the effort might never occur. They also offer a certification, so if you are looking for a change management resource this is a good way to narrow down your search.
There are also several processes for change management that you can apply and align well with the ACMP standard. As you create your strategy, determine which process, or processes you might leverage to help with driving change based on the culture of your organization.
Changefirst
Changefirst is a methodology that breaks change management into efforts at the organizational level and efforts that must occur locally. Organizationally:
- The shared change purpose is the aspirational message that the leadership must be onboard to deliver to the organization to motivate the people that must change to change.
- Effective change leadership is the plan you develop to guide the change effort.
- The powerful engagement processes are the implementation or activation of the plan.
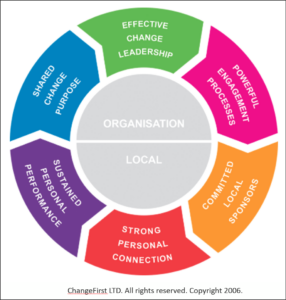
The local efforts:
- Local sponsors are the hammer that drives the change at the end-user level.
- Build a strong personal connection so the person that must change knows and feels they must change.
- Sustained personal performance is about monitoring the people that are changing to collect feedback and make needed adjustments.
Using multifactor authentication rollout as the change, here is an example of what Changefirst might look like:
Our case for change is to change authentication so that we strengthen the verification process during end-user authentication while balancing security and end-user productivity. We propose we roll out multifactor authentication (MFA) across the organization.
- To be successful, we must enroll HR leadership to provide the MFA and training to new hires, delivery, and operations team leads to train support staff, and use a common authentication mechanism across all solutions.
- During an all-hands, leadership must announce their support and endorsement of zero trust and spotlight it as a big annual initiative for the organization.
- We must plan a local “road show” going to the list of key stakeholders to present the zero-trust initiative and get their support.
- For annual reviews, we must include a personal review goal that rolls up to achieving zero trust KPIs.
- Provide ongoing training and presentations by experts on best practices using MFA and create a feedback mechanism to solicit suggestions for improvement.
Changefirst has two methodologies on its website. For change management, you are interested in People-Centered Implementation (PCI). There are online assets you can purchase with templates and tools for using the methodology. There’s a short (3-minute) video that introduced the process or you can download a whitepaper from their site that provides additional explanation. To download, you must register, and they email you a link that you use to access the 40-page eBook.
Kotter-Cohen
The Kotter framework has been around for almost twenty years so there is a lot of expertise and guidance available. The framework has eight steps for leading change:
- Create a sense of urgency is “setting the house on fire” and is the message that you ask the leadership team to deliver.
- Build a guiding coalition is about building out or assigning change management functions to the core team if the core team will drive the change.
- Form a strategic vision is about defining the vision or goal of the change management process to drive adoption of the technical implementation.
- Enlist a volunteer army focuses on finding the people that will help drive the change and the influencers that everyone in the organization naturally follows.
- Enable action by removing barriers involves running a pilot and then a stepped rollout plan and determining what must change in order to continue rolling out and gaining adoption.
- Generate short-term wins focuses on getting successful adoption by a group of people and using them as poster children to inspire others to change.
- Sustain acceleration is about creating a plan to continue driving the change after the luster of the short-term win starts to tarnish.
- Institute change aims to put mechanisms in place that force the change to stick over time, whether that is through rhythmic training, review process inclusion, or other methods.
Using the MFA example, it might look like this:
The external threat to our IT environment and our data requires we change our user verification to defend against attacks from bad actors. We must change authentication so that we strengthen the verification process during end-user authentication while balancing security and end-user productivity. We propose we roll out multifactor authentication (MFA) across the organization following these steps:
Increase Urgency: Negotiated new hire orientation training and provisioning of MFA as part of the onboarding process by <date>
Build the Guiding Team: Onboard stakeholders from HR, Training, Identity Dev, IT Ops, and Ops teams to kick off.
Get the Right Vision: Stakeholders create or agree to the existing mission and vision for MFA.
Communicate for Buy-in: Socialize plan with sponsors, organizational leaders, and members of training, delivery, operations, and support teams.
Empower Action: Provide roadmap, architecture, constraints, and other critical information, and inform “boots on ground” teams where they must confirm and where they can stray from the plan.
Create Short-term Wins: Create and alpha test MFA capability with key stakeholders and early adopters.
Don’t Let Up: Security moment at every sprint review and sprint planning meeting.
Make it Stick: Publish refresh training forward schedule for the next two years with HR for internal training.
On the Kotter website are all the resources you might need to be successful. There is only one framework, however, there are also a set of change principles listed as well. On the 4 Core Change Principles webpage are a link to download an eBook and a series of short videos to describe the principles. We recommend you review the videos (4 minutes each) and download the eBook. To download the eBook, you must fill out a form and they will email a link to the eBook.
Prosci ADKAR
ADKAR is the acronym for awareness, desire, knowledge, ability, and reinforcement which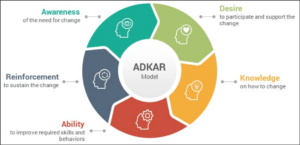 happen to be the steps in their process. Many consultancies use ADKAR as their change management process:
happen to be the steps in their process. Many consultancies use ADKAR as their change management process:
- Awareness focuses on building awareness of the need to change and messaging the nature of change.
- Desire is about creating a carrot big enough that people want to support the change, as well as participate and engage in the change.
- Knowledge defines how to change and how to implement a new set of skills and behaviors.
- Ability on getting the skills in place and removing any blockers to implement and adopting the change and demonstrating the performance of the change.
- Reinforcement aims to put the mechanisms in place to sustain the change and to build culture and competence around the change.
Using the MFA example, it might look like this:
For this initiative, we must change authentication so that we strengthen the verification process during end-user authentication while balancing security and end-user productivity. We propose we roll out multifactor authentication (MFA) across the organization. We will use the following change management process:
- Awareness: We are going to drive awareness of the need for change by stating we must implement MFA because we assume we have been hacked and are still vulnerable
to attacks. - Desire: We need you to set an example by using MFA in a visible manner, quickly migrating to MFA for groups of accounts, and by updating any of your applications you can to MFA authentication.
- Knowledge: Take the available training on MFA or if you are an expert, host a lunch-and-learn to grow others. If possible, host a hackathon to grow our community of technologists’ skills for MFA and produce innovations for its usage.
- Ability: Implement MFA and provide visibility to metrics that show the impact using numbers.
- Reinforcement: Consider doing a presentation on the impact of MFA during team meetings or all-hands meetings.
Prosci has a few models and processes listed on their site. This one is easy to implement and meant to drive individual change. They also have a nice primer for change management. You register and are sent a link to the actual 17-page eBook. They also have a set of six resources you can register to download that help with ADKAR. When you register for this resource, a zip file containing the six PDFs is downloaded to your device. Each file is about 3MB.
VitalSmarts Crucial Learning Influencer
Influencer is a model designed to change ingrained human behavior. The other frameworks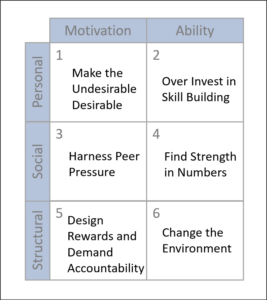 presented feel like the requisite change is in the center of the framework and the people are at the edges. This framework feels like it is centered on the human behavior that must change and the change is on the edge. The columns are broken into defining how to motivate people to change their behavior and what competence must be added using what manner. The rows describe the level of change from the individual to the herd, and then to structure.
presented feel like the requisite change is in the center of the framework and the people are at the edges. This framework feels like it is centered on the human behavior that must change and the change is on the edge. The columns are broken into defining how to motivate people to change their behavior and what competence must be added using what manner. The rows describe the level of change from the individual to the herd, and then to structure.
Using the MFA example, it might look like this:
For this initiative, we are introducing multifactor authentication. We propose we roll out multifactor authentication (MFA) across the organization providing it first to influencers and then using gamification with a reward of personal perks to motivate adoption. We’ll use the following motivators to grow the abilities:
- Personal Motivation: Enable BYOD devices and work-from-home scenarios for people using MFA. Set up a trivial pursuit-style quiz with the top scorers at the top of the list for receiving MFA capability.
- Personal Ability: Funding for training and certification, gamification, and prizes for internal leaders in growing and sharing knowledge. Set up a badge or signage program so local individuals for each product team or group can become the “floor Expert”.
- Social Motivation: Make the MFA device an employee status symbol. Award custom phone cases and badges in the employee directory to apply peer pressure.
- Social Ability: Sponsor lunch-and-learn or hackathons for MFA development and improvement. Have the Floor Expert drive the events and act as a liaison that provides feedback to the core team.
- Structural Motivation: Implement a “bench” program to replace people not meeting commitments in adopting MFA. Assign a temporary backup to fill their role temporarily so they have the opportunity to grow their competence in using the MFA-enabled devices. The person that provides the backfill strengthens their skill while the people in remedial training realize there are consequences.
- Structural Ability: Shift MFA from being an optional or role-based requirement to being the required authentication method for everyone. This is setting up policy and standard operating procedure (SOP) that requires adoption. SOPs and policies are almost always driven by a nameless “They” who is requiring the policy. And it really doesn’t matter whether the “They” is internal or external, good or bad actors. It is simply someone that makes this required change beyond local control.
Vitalsmarts did have a model named Influencer. It is now part of the Crucial Learning set of courses (good courses) so it is a bit harder to find a lot of information online. This diagram represents the model when it was driven by Vitalsmarts.
Crucial Learning has books and courses, and a YouTube channel, but to effectively use it you need to pay for some training and invest time in formal education on change management. We recommend if you use this framework that you find a consultant with experience driving initiatives with this process.
Final Thoughts on Change Management
With Zero Trust, change will be constant and forever so a goal of change management should include creating a culture of change. Most people like routine work where they gain competence in their role and focus their career on execution. Creating a culture where change is constant and is not limited to Zero Trust can help.
